eJPT Assessment Methodologies: Vulnerability Assessment CTF 1 — Walkthrough & Insights
Lab Environment
In this lab environment, you will have access to a target machine available at http://target.ine.local. Additionally, a Nessus dashboard is set up for vulnerability scanning and can be accessed via https://localhost:8834/. Use the provided credentials to log into the Nessus dashboard for further analysis.
Credentials:
1
2
Username: admin
Password: adminpasswd
Objective: Identify the services running on the machine, perform a detailed vulnerability scan, and capture all the flags hidden within the environment.
Flags to Capture:
- Flag 1: Explore hidden directories for version control artifacts that might reveal valuable information.
- Flag 2: The data storage has some loose security measures. Can you find the flag hidden within it?
- Flag 3: A PHP file that displays server information might be worth examining. What could be hidden in plain sight?
- Flag 4: Sensitive directories might hold critical information. Search through carefully for hidden gems.
Tools
The best tools for this lab are:
- Nmap
- Nessus
Note
In this lab, the flag will follow the format: FLAG1MD5Hash. For example, FLAG1_0f4d0db3668dd58cabb9eb409657eaa8. You need to submit only the MD5 hash string, excluding the underscore (). For instance: 0f4d0db3668dd58cabb9eb409657eaa8.
Question 1:
Let’s start with the first question with is Explore hidden directories for version control artifacts that might reveal valuable information. starting with nmap command.
1
nmap -A --min-rate=10000 target.ine.local | tee user_Nmap-A.txt
which revels quite a good number of areas where i can focus on which it found a .git repo on the web service running on the host on the port 80 and here is the nmap output.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
root@INE:~# nmap -A --min-rate=10000 target.ine.local
Starting Nmap 7.92 ( https://nmap.org ) at 2025-03-24 10:13 IST
Nmap scan report for target.ine.local (192.145.226.3)
Host is up (0.000075s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
| http-git:
| 192.145.226.3:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
| Remotes:
|_ https://github.com/fermayo/hello-world-lamp.git
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
| http-robots.txt: 8 disallowed entries
| passwords/ config.inc classes/ javascript/
|_owasp-esapi-php/ documentation/ phpmyadmin/ includes/
3306/tcp open mysql MySQL 5.5.47-0ubuntu0.14.04.1
| mysql-info:
| Protocol: 10
| Version: 5.5.47-0ubuntu0.14.04.1
| Thread ID: 9
| Capabilities flags: 63487
| Some Capabilities: SupportsLoadDataLocal, SupportsTransactions, InteractiveClient, ConnectWithDatabase, IgnoreSigpipes, DontAllowDatabaseTableColumn, Speaks41ProtocolOld, SupportsCompression, FoundRows, LongPassword, Speaks41ProtocolNew, LongColumnFlag, ODBCClient, IgnoreSpaceBeforeParenthesis, Support41Auth, SupportsMultipleResults, SupportsAuthPlugins, SupportsMultipleStatments
| Status: Autocommit
| Salt: N3R&a;@o0A4~Ds:elpmQ
|_ Auth Plugin Name: mysql_native_password
MAC Address: 02:42:C0:91:E2:03 (Unknown)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.08 ms target.ine.local (192.145.226.3)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.47 seconds
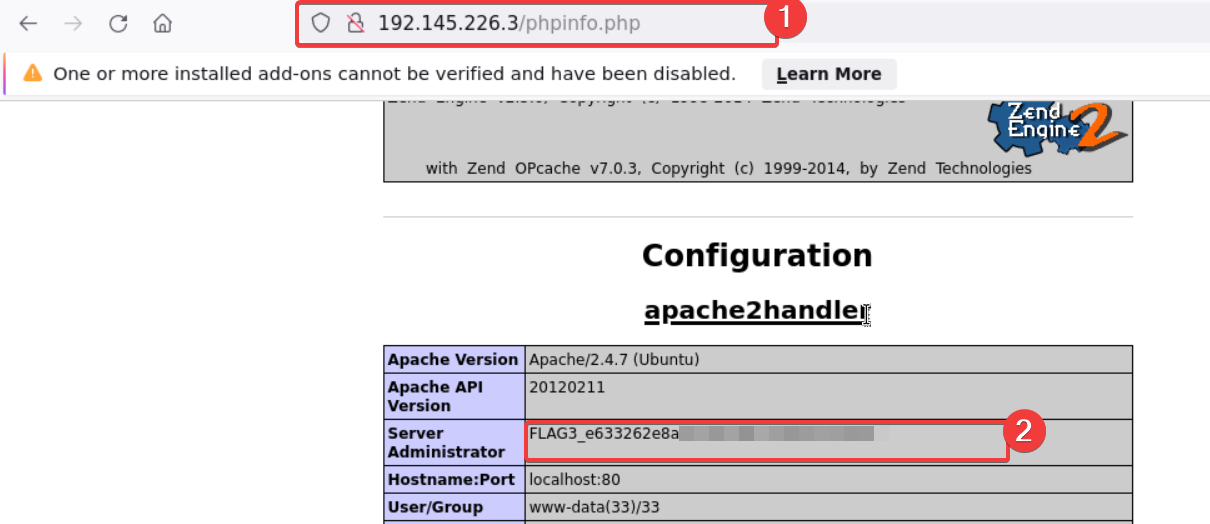
Since the git is there let’s take a look on that and found the flag1 setting right there! 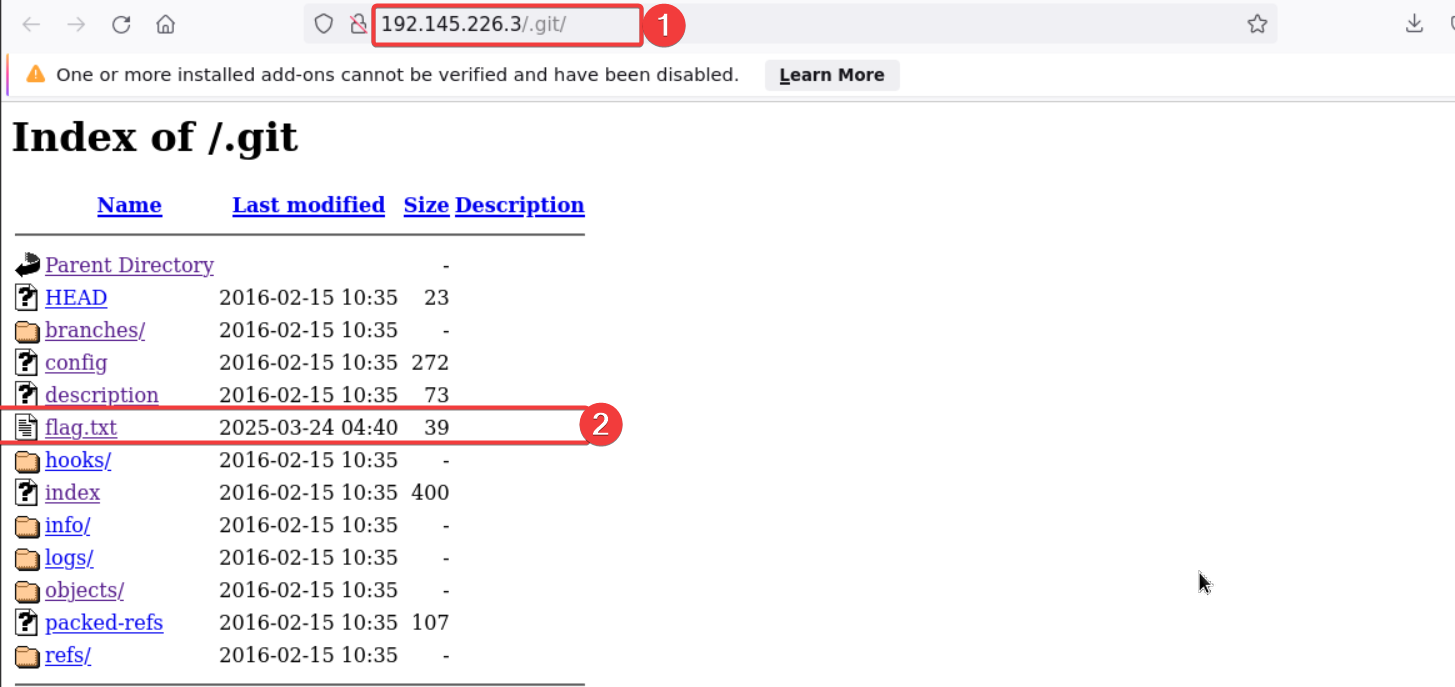
Question 2:
The data storage has some loose security measures. Can you find the flag hidden within it?
based on the question it says that its a data storage which means it’s much be from database services and in here we found a SQL services running with the help of Nmap scans results. and now let’s also the the target robots.txt hence it could have hold of any services that worth for us. and by doing so there is the disallowed directory called phpmyadmin and that is open without any creds to it, in plain so we navigate into it 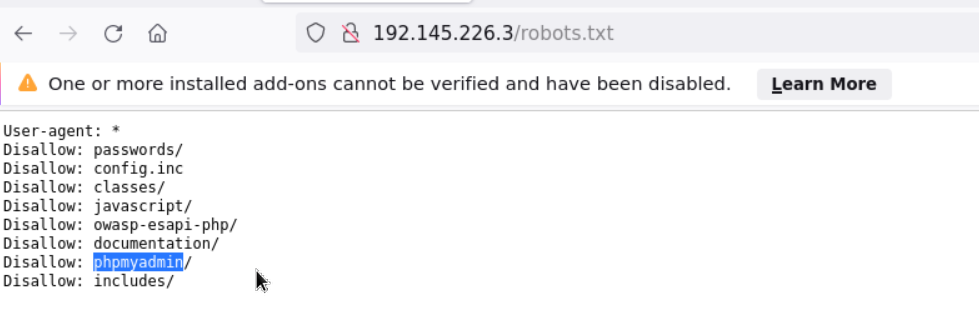 By navigating through the php and found a database as
By navigating through the php and found a database as mysql and also found a table called secret_info by looking into the table i got the flag_2! 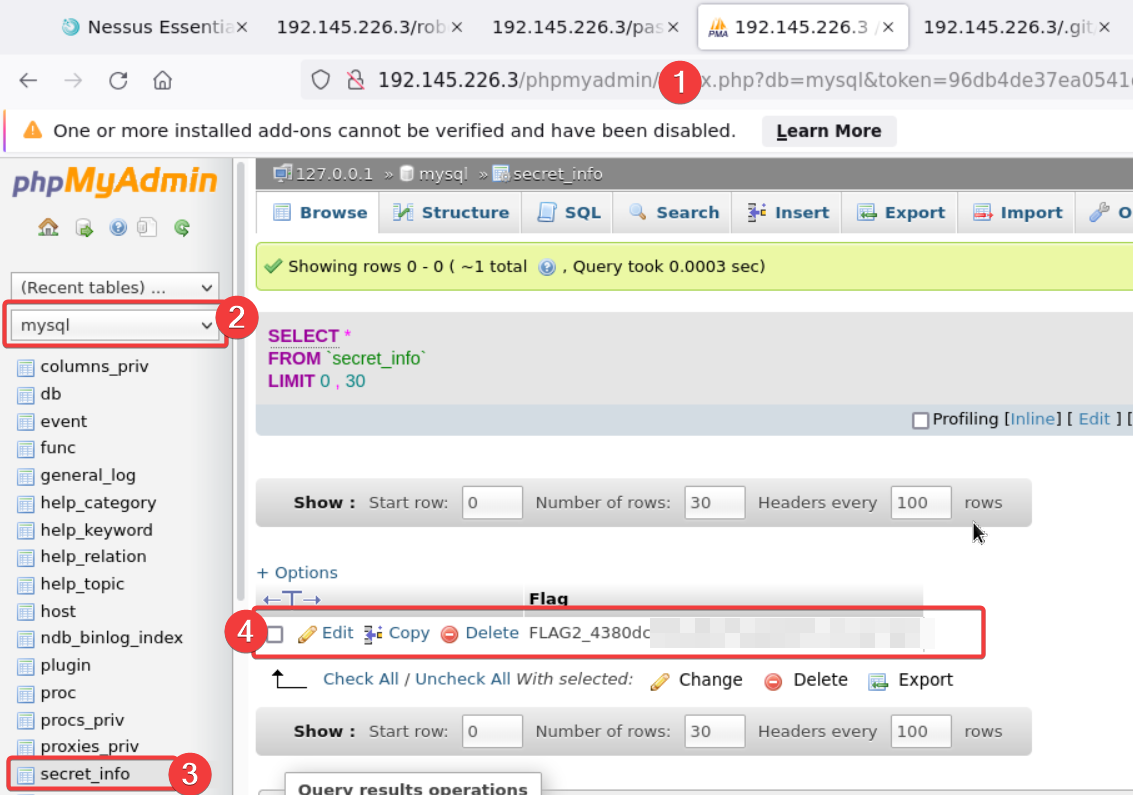
Question 3:
A PHP file that displays server information might be worth examining. What could be hidden in plain sight?
based on the question I found that i should be looking for the filetype as php on the target. so i have used the fuff tool which helps me to go through the directory and find the specific file i was looking for, here is the command i would works.
1
ffuf -u http://target.ine.local/FUZZ -w /usr/share/seclists/Discovery/Web-Content/big.txt -e .php -c -mc 200
Description: This ffuf command is performing a directory and file brute-force attack against the target web application at http://target.ine.local/ to discover hidden files and directories.
Breakdown:
-u http://target.ine.local/FUZZ→ The target URL whereFUZZacts as a placeholder for brute-force attempts.-w /usr/share/seclists/Discovery/Web-Content/big.txt→ Uses thebig.txtwordlist from SecLists for fuzzing.-e .php→ Appends.phpas an extension to each word in the wordlist.-c→ Enables colored output for better readability.-mc 200→ Filters results to show only responses with HTTP status 200 (OK).
 the phpinfo is looks like answer to from the question
the phpinfo is looks like answer to from the question A PHP file that displays server information and so by checking out i found the flag3!
Question 4:
Sensitive directories might hold critical information. Search through carefully for hidden gems.
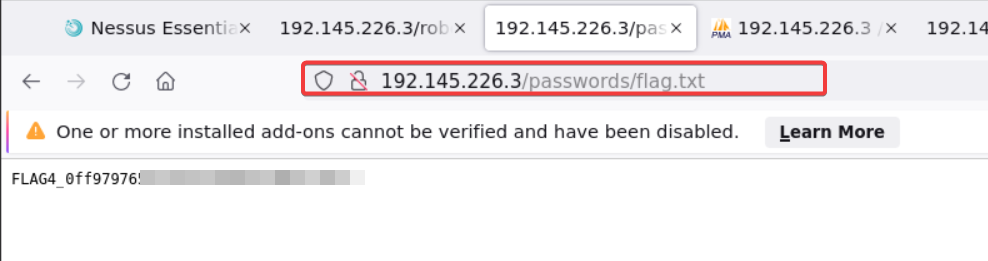
Since this question all about navigating through the directory let’s take a look at robots.txt and take a look into the password directory and hooray I found the last flag sitting over there waiting to be discovered! 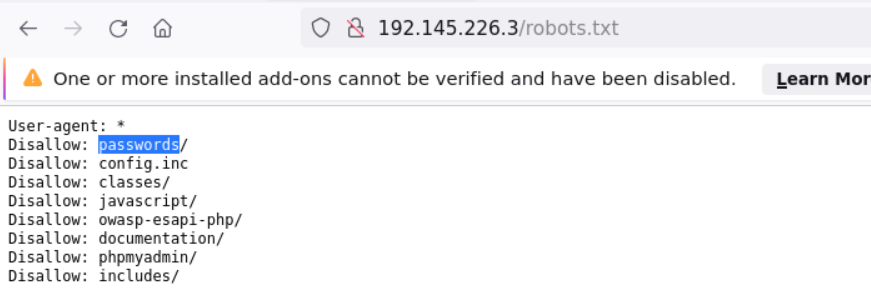

With that I finished the lab work for this modules. let’s move to next chapter in this field of security.